As an organization who focuses on compliance, specifically NIST 800-171 and CMMC, we found ourselves in a predicament when it came to aligning the systems we use to support clients with the requirements in NIST/CMMC – the dreaded FIPS mode. In this article we will focus on Fortinet’s FortiManager.
The function of being able to send FortiGate (FGT for short) logs to a FortiManager (FMG for short) breaks when the FMG has FIPS enabled. An error of OFTP validation/verification failed is one of the errors, but all the errors reference the OFTP engine.
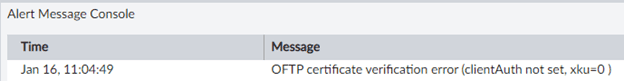
Message: OFTP SSL Error: remote_ip=x.x.x.x, error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
After spending many hours researching this and working with multiple Fortinet support reps we found one that was able to help us and with some additional tweaks were able to get logging working again. Hopefully this information will help anyone else in a similar situation
Steps we followed.
Setup:
-created a directory called “ca” to act as the primary directory to run the next commands from
-Copy the openssl openssl.cnf file in the ca directory. open it in a text editor. In the [ CA_default ] section, change the “dir” line to point to the absolute path of your “ca” directory
-within “ca”, created subdirectories “certs” “crl” “csr” “newcerts” “private”
-in the “ca” directory, created blank file “index.txt” and two files with just “1000” in them “serial” and “crlnumber”. (each of those serial and crlnumber files has no extension, but could be created in notepad and just type 1000 in them and save)
1-Setup a CA cert and key
2-Create a server private key
3-Generate a CSR for server cert
4-Sign the server cert **note when performing this step, you MUST utilize the “-cert” switch and point to the CA certificate you created in Step 1
Example: openssl ca -config openssl.cnf -extensions server_cert -days 375 -notext -md sha256 -cert certs/ca-cert.pem -in csr/fmgserver-cert-csr.pem -out certs/fmgserver-cert-cert.pem
5-Create server cert pfx
6-Create client cert key
7-Create client cert csr
8-Sign client cert **note when performing this step, you MUST utilize the “-cert” switch and point to the CA certificate you created in Step 1
9-Create client pfx
10-Import client cert as a pfx onto the FGT
11-Import the CA cert as a CA cert onto the FGT
12-Import the CA cert as a CA cert onto the FMG
13-Import the server cert as a Local PFX onto the FMG
14-Import the client cert as Remote onto the FMG
15-Set the FMG to use the server cert
Config sys cert oftp
Set mode local
Set local <server cert name>
end
16-Set the FGT to use the client cert
Config log fortianalyzer setting
Set certificate <client cert name)
Set certificate-validation disabled
end
After completing these steps, the FGT logs should successfully reach, and be accepted by, the FMG server. Verify in FMG under Log View, your FGT devices should show